Homepage | Activities | Events | Lists | Development | Translate | Contact
Difference between revisions of "Features/WPA-WPA2-Enterprise-Network-Connections/Testing"
Jump to navigation
Jump to search
| Line 18: | Line 18: | ||
**[[File:router_configuration.png]] | **[[File:router_configuration.png]] | ||
* Note that, you may only need to enter the "Radius Server IP Address" ("192.168.1.3" in the screenshot). The "Radius Server Port", and "Share Secret" are the default ones (at least for a default setup of freeradius). | * Note that, you may only need to enter the "Radius Server IP Address" ("192.168.1.3" in the screenshot). The "Radius Server Port", and "Share Secret" are the default ones (at least for a default setup of freeradius). | ||
| + | |||
| + | == TESTING - TTLS-based authentication == | ||
| + | * Navigate to the "Neighbourhood view" on the XO. | ||
| + | * Click on the network-icon, and enter the parameters, as seen in the following screenshot | ||
Revision as of 09:06, 14 December 2011
Setting up a RADIUS server (on a dedicated machine)
- Install "freeradius" rpm package
- sudo yum install freeradius
- Modify "/etc/raddb/clients.conf", to include the name of the network access-point/router. Sample files are present at
- Modify "/etc/raddb/users", to configure a username-password pair for authentication. Sample files are present at
- Start the server, by issuing the following command
- sudo /usr/sbin/radiusd -X &
Setting up the access-point / router
- Connect the access-point/router, with the RADIUS server machine, through a ethernet cable.
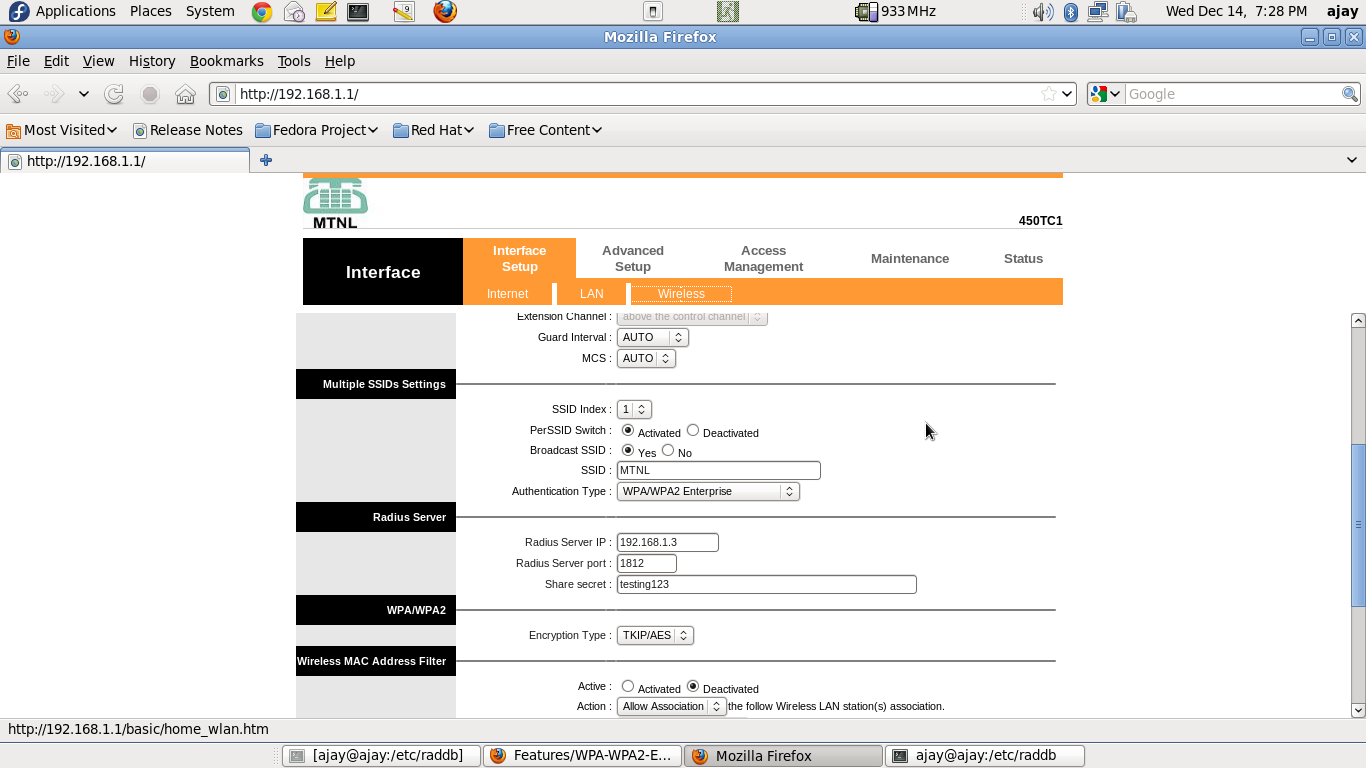
- Through the RADIUS server machine, open the browser, type in the access-point/router IP address, and configure it for WPA/WPA2-Enterprise authentication. A sample screenshot is presented below
- Note that, you may only need to enter the "Radius Server IP Address" ("192.168.1.3" in the screenshot). The "Radius Server Port", and "Share Secret" are the default ones (at least for a default setup of freeradius).
TESTING - TTLS-based authentication
- Navigate to the "Neighbourhood view" on the XO.
- Click on the network-icon, and enter the parameters, as seen in the following screenshot