Features/WPA-WPA2-Enterprise-Network-Connections: Difference between revisions
No edit summary |
|||
| Line 5: | Line 5: | ||
[[Category:Features requested by School Xyz|<Feature Name>]] (the |Feature Name option sorts the entry on the category page under the first letter of <Feature Name>). --> | [[Category:Features requested by School Xyz|<Feature Name>]] (the |Feature Name option sorts the entry on the category page under the first letter of <Feature Name>). --> | ||
</noinclude> | </noinclude> | ||
<!-- All fields on this form are required to be accepted. | <!-- All fields on this form are required to be accepted. | ||
Revision as of 06:43, 14 December 2011
Summary
This feature helps connect to WPA/WPA2-Enterprise Networks, in a sugar-environment.
Owner
- Name: Ajay Garg, Anish Mangal, Sascha Silbe
- Email: ajay@activitycentral.com, anish@activitycentral.com, silbe@activitycentral.com
Current status
- Targeted release: (SUGAR_VERSION)
- Last updated: (DATE)
- Percentage of completion: XX%
Detailed Description
Expand on the summary, if appropriate. A couple of sentences suffices to explain the goal, but the more details you can provide the better.
Benefit to Sugar
What is the benefit to the platform? If this is a major capability update, what has changed? If this is a new feature, what capabilities does it bring? Why will Sugar become a better platform or project because of this feature?
Make sure to note here as well if this feature has been requested by a specific deployment, or if it has emerged from a bug report.
Scope
What work do the developers have to accomplish to complete the feature in time for release? Is it a large change affecting many parts of the distribution or is it a very isolated change? What are those changes?
UI Design
Does the feature have a direct impact on the work flow, or does it need a UI? Link here mockups, or add detailed descriptions.
How To Test
Setting up a RADIUS server (on a dedicated machine)
- Install "freeradius" rpm package
- sudo yum install freeradius
- Stop the server (if running)
- sudo killall radiusd
- Modify "/etc/raddb/clients.conf", to include the name of the network access-point/router. Sample files are present at
- Modify "/etc/raddb/users", to configure a username-password pair for authentication. Sample files are present at
- Fedora 17 users, please run the following command, before starting the radius server:
- sudo mv /etc/raddb/modules/dhcp_sqlippool ~
- Start the server, by issuing the following command:
- sudo /usr/sbin/radiusd -X &
Setting up the access-point / router
- Connect the access-point/router, with the RADIUS server machine, through a ethernet cable.
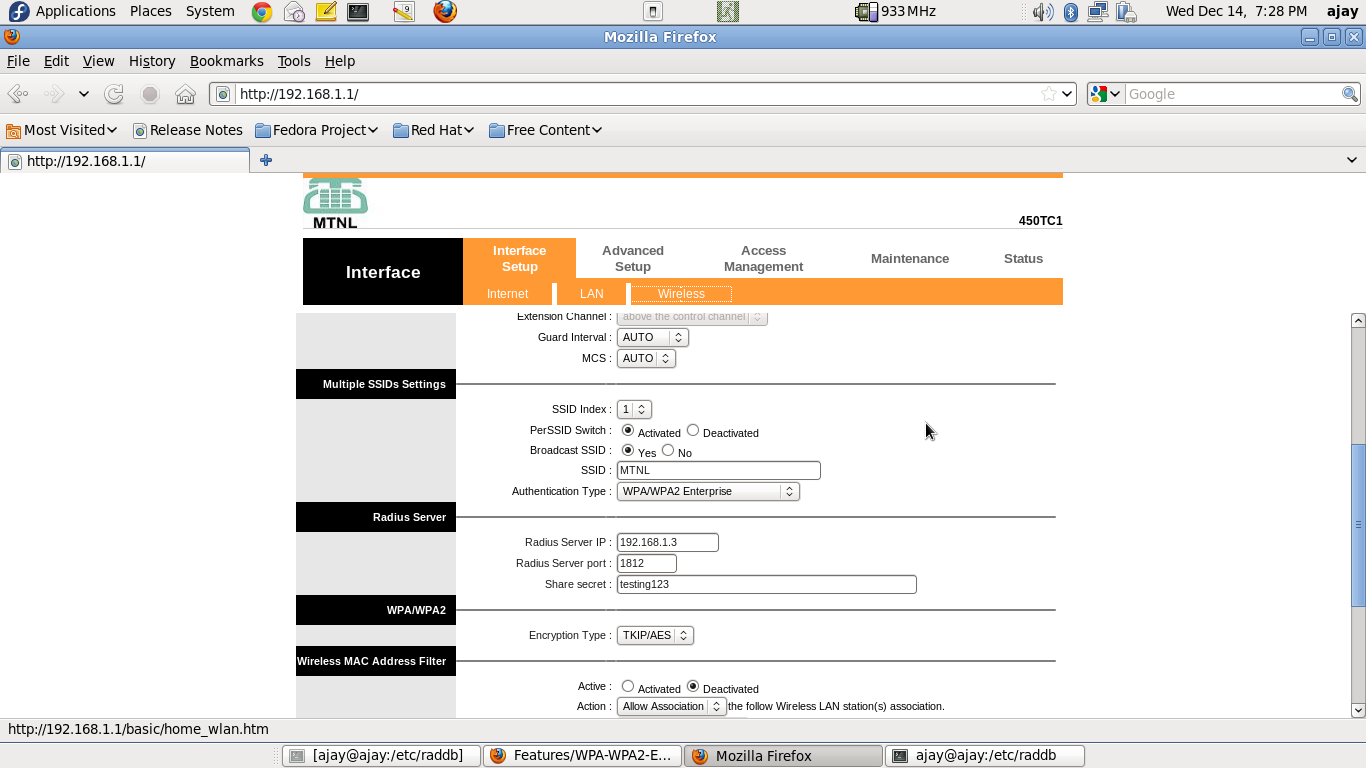
- Through the RADIUS server machine, open the browser, type in the access-point/router IP address, and configure it for WPA/WPA2-Enterprise authentication. A sample screenshot is presented below
- Note that, you may only need to enter the "Radius Server IP Address" ("192.168.1.3" in the screenshot). The "Radius Server Port", and "Share Secret" are the default ones (at least for a default setup of freeradius).
Connecting a client - TLS-based authentication
- Make sure you have three certificates - user-certificate, ca-certificate, private-key - before you proceed. One way to get these certificates is as follows:
- Go to the RADIUS server machine, and navigate to "/etc/raddb/certs"
- Run the following commands
- sudo make client.pem
- sudo chmod 0644 client.p12
- sudo chmod 0644 ca.pem
- Transfer "client.p12" and "ca.pem" to a USB drive.
- Use this USB drive, in the subsequent steps.
- Navigate to the "Neighbourhood view" on the XO.
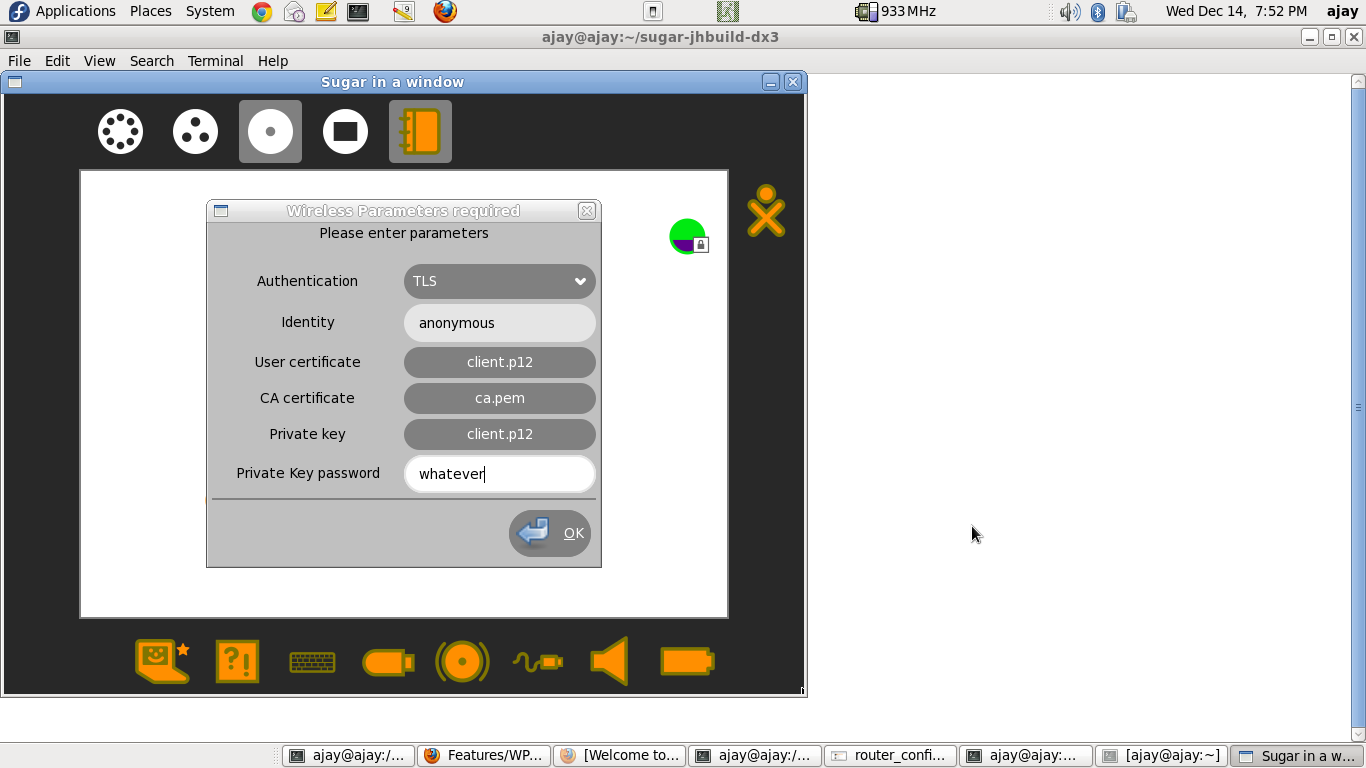
- Click on the network-icon, and enter the parameters, as seen in the following screenshot
- NOTES
- If either of "User Certificate", or "Private Key" is in ".p12" format, both these entries should be EXACTLY equal, since the ".p12" certificate contains both.
- For entering the "User certificate", "CA certificate" and "Private Key", you will be taken to the "Journal-Chooser". You may use the certificates that were retrieved earlier.
Connecting a client - LEAP-based authentication
- Help required !!!!
- We have not been able to set-up a LEAP-authentication-supported access-point / router.
- Any CISCO guys !!??
Connecting a client - TTLS-based authentication
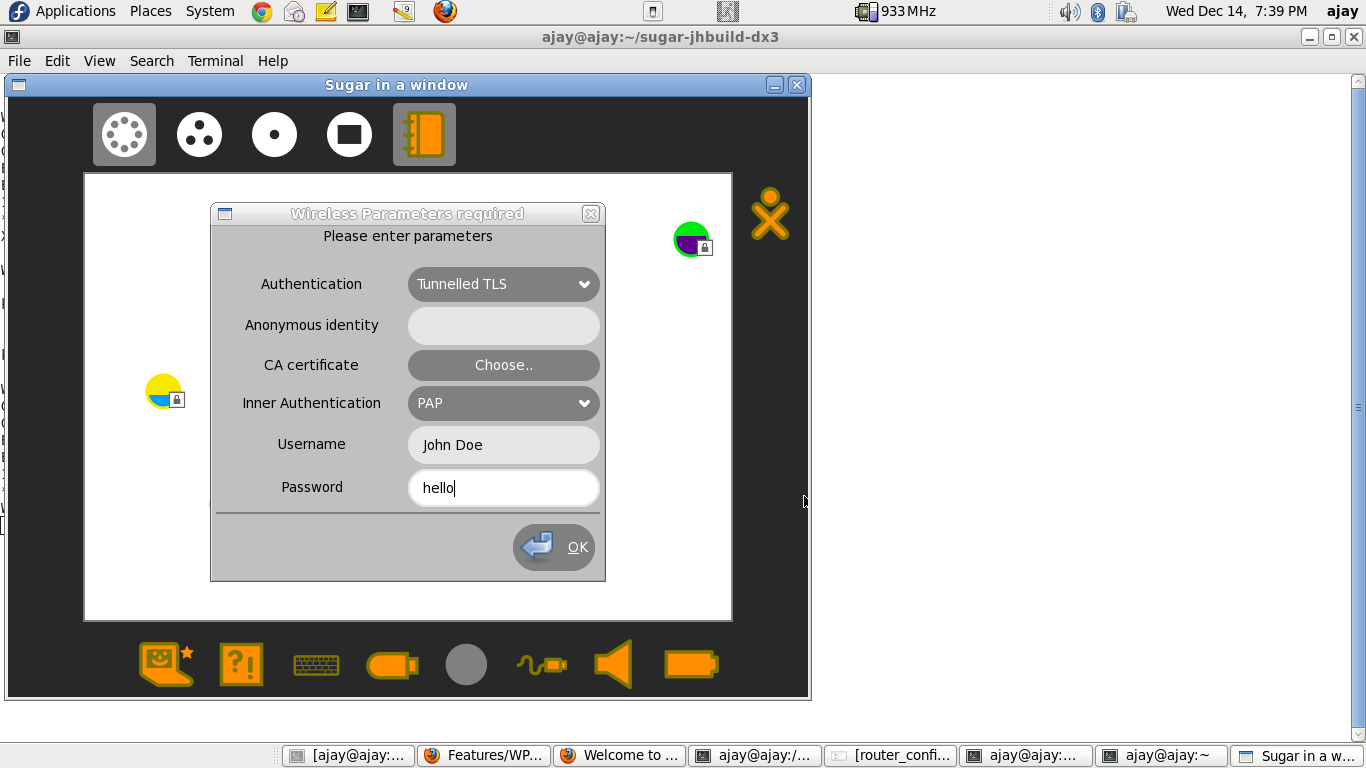
- Navigate to the "Neighbourhood view" on the XO.
- Click on the network-icon, and enter the parameters, as seen in the following screenshot (thanks to Anish, for showing me this minimal configuration).
- NOTES
- The above configuration is a minimalistic configuration. However, the parameters-cum-secrets modal-dialog, has been modelled on nm-applet.
Connecting a client - PEAP-based authentication
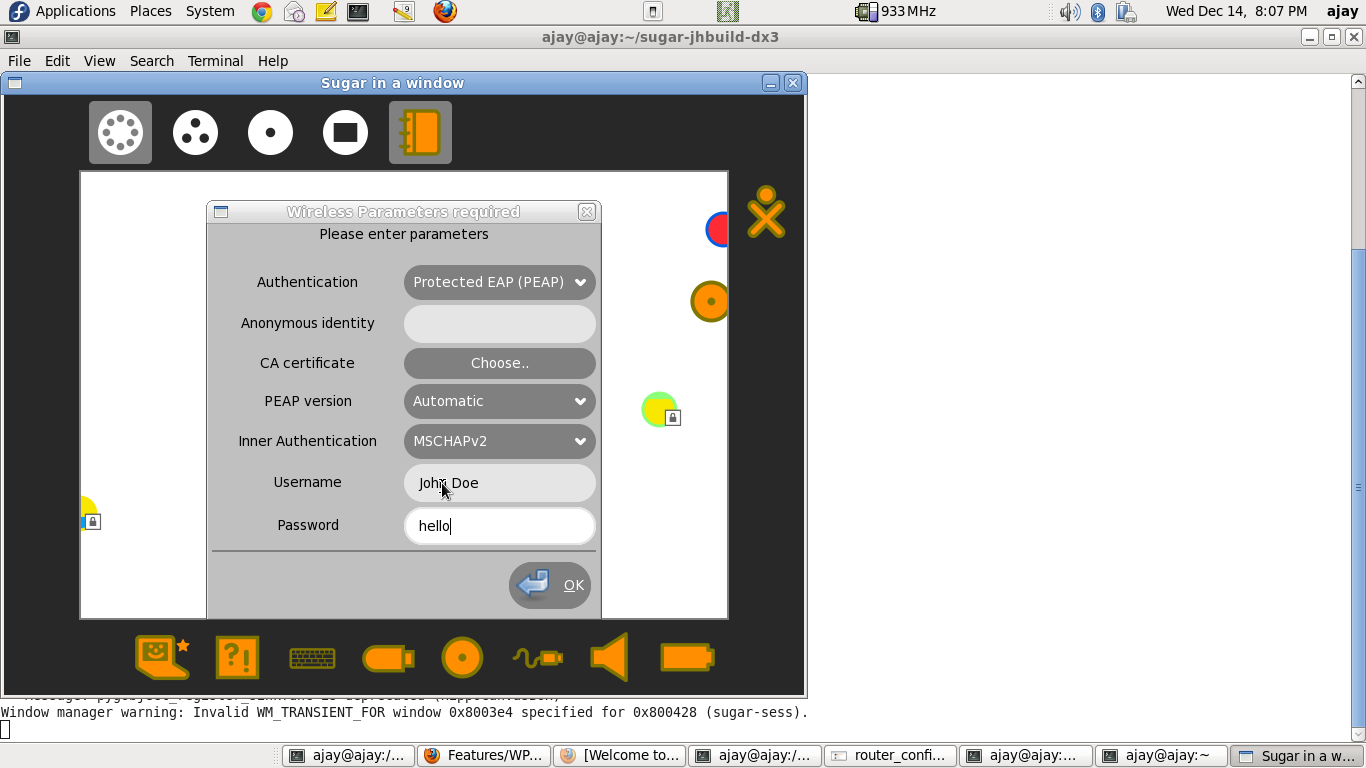
- Navigate to the "Neighbourhood view" on the XO.
- Click on the network-icon, and enter the parameters, as seen in the following screenshot.
- NOTES
- The above configuration is a minimalistic configuration. However, the parameters-cum-secrets modal-dialog, has been modelled on nm-applet.
User Experience
If this feature is noticeable by its target audience, how will their experiences change as a result? Describe what they will see or notice.
Dependencies
What other packages (RPMs) depend on this package? Are there changes outside the developers' control on which completion of this feature depends? In other words, does your feature depend on completion of another feature owned by someone else or that you would need to coordinate, which might cause you to be unable to finish on time? Other upstream projects like Python?
Contingency Plan
If you cannot complete your feature by the final development freeze, what is the backup plan? This might be as simple as "None necessary, revert to previous release behaviour." Or it might not. If your feature is not completed in time, we want to assure others that other parts of Sugar will not be in jeopardy.
Documentation
Is there upstream documentation on this feature, or notes you have written yourself? Has this topic been discussed in the mailing list or during a meeting? Link to that material here so other interested developers can get involved.
Release Notes
The Sugar Release Notes inform end-users about what is new in the release. An Example is 0.84/Notes. The release notes also help users know how to deal with platform changes such as ABIs/APIs, configuration or data file formats, or upgrade concerns. If there are any such changes involved in this feature, indicate them here. You can also link to upstream documentation if it satisfies this need. This information forms the basis of the release notes edited by the release team and shipped with the release.